Many of my servers run under the Proxmox virtual environment. For servers that doesn’t have a dedicated IP available for its guests I use iptables based NAT network to forward packets as described in my previous article: https://manatails.net/blog/2018/04/running-proxmox-with-nat/
But I came across a problem where Windows guests detect the network as ‘Unknown’ and try to create a new network profile every reboot.
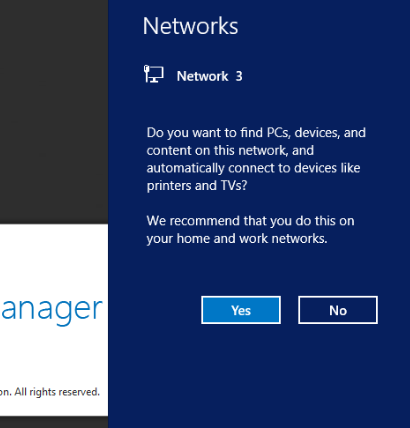
Not only it looked bad to have random names ‘Network 18’, but also the network type defaults to public network so any rules in private network get ignored until I manually set the network type to private.
I looked a bit in depth and found that the feature is called ‘Network Location Awareness’ per the original article https://msdn.microsoft.com/en-us/library/aa480195.aspx
From the page:
Digital Subscriber Line (DSL) and cable modems typically act as network address translators (NATs). As a result, their MAC addresses can be used to uniquely qualify the user’s network. NLA uses the MAC address of the user’s DSL or cable modem as the link ID.
Practically, Windows was using the MAC address of the default gateway to diffrentiate the network.
So I had to give the NAT interface a unique MAC address in order to be recognized.
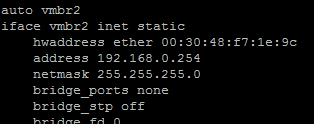
Add ‘hwaddress ether’ to the interface config and give a random mac address, then windows will consistently identify the network.
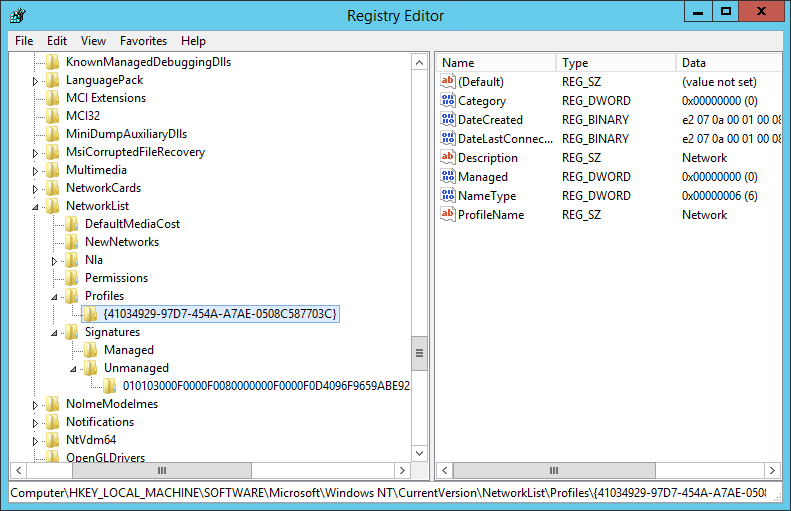
Finally open regedit and go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList then delete all entries in Profiles and Signatures to get rid of previously detected networks and reset the counter.